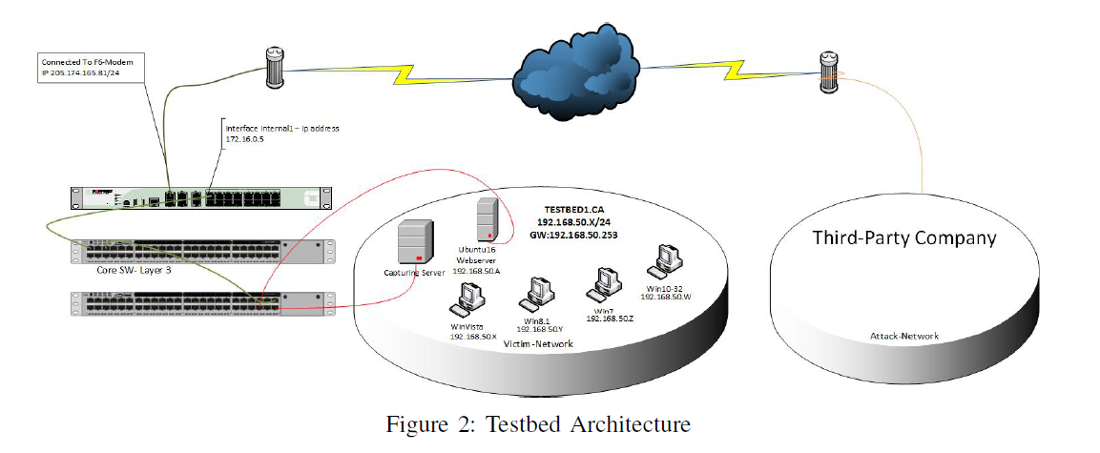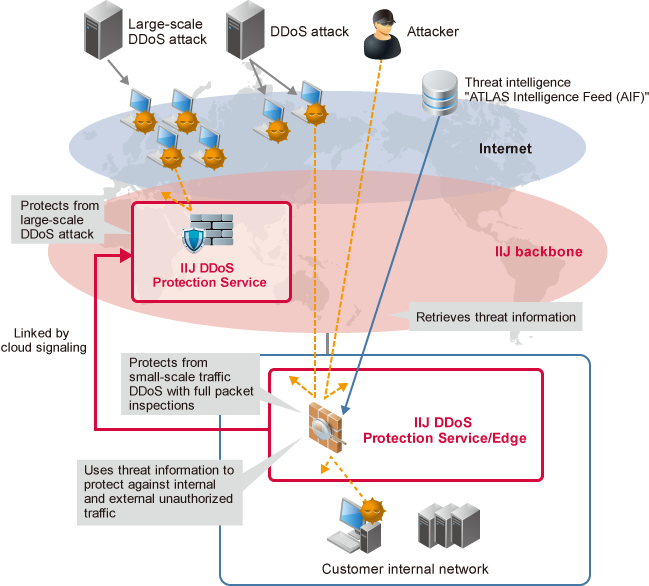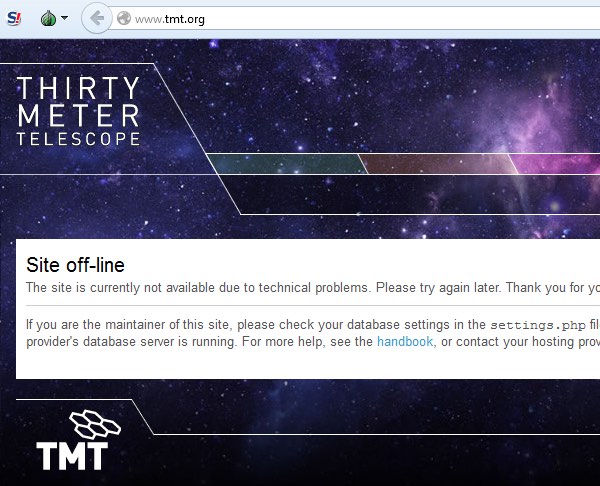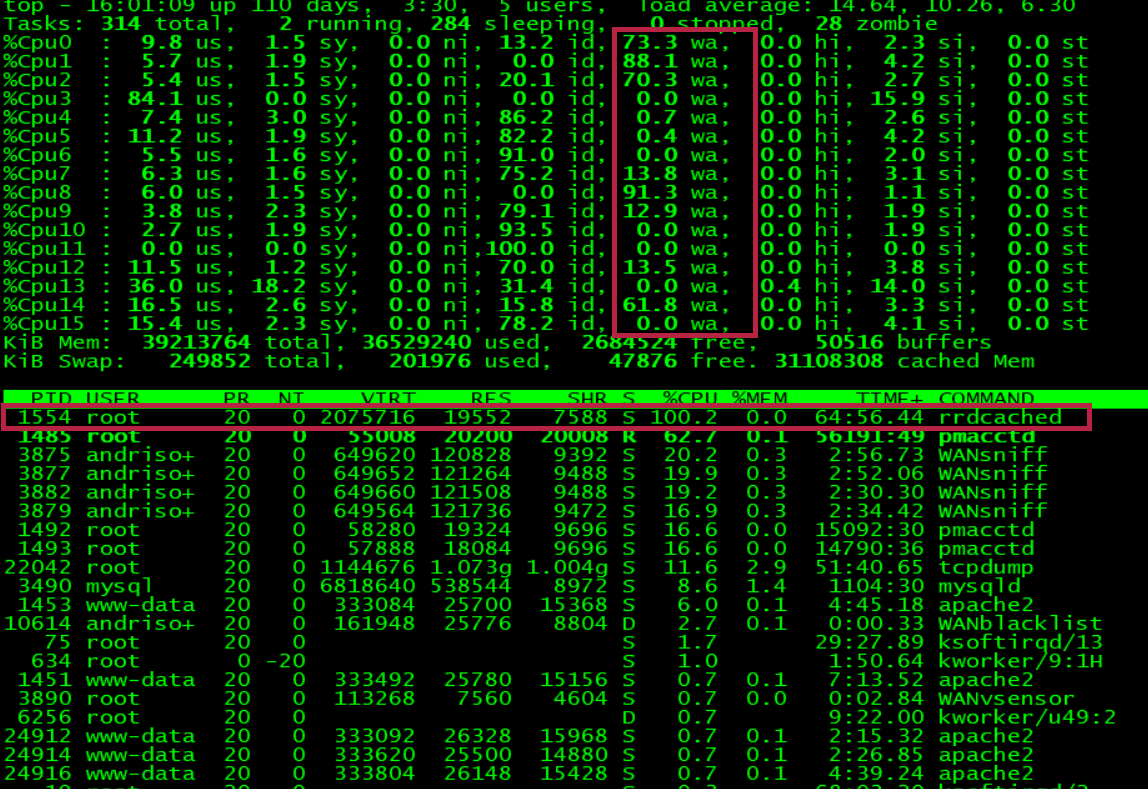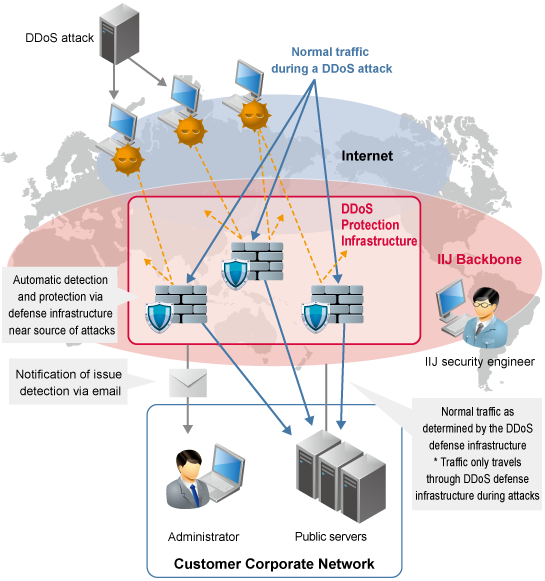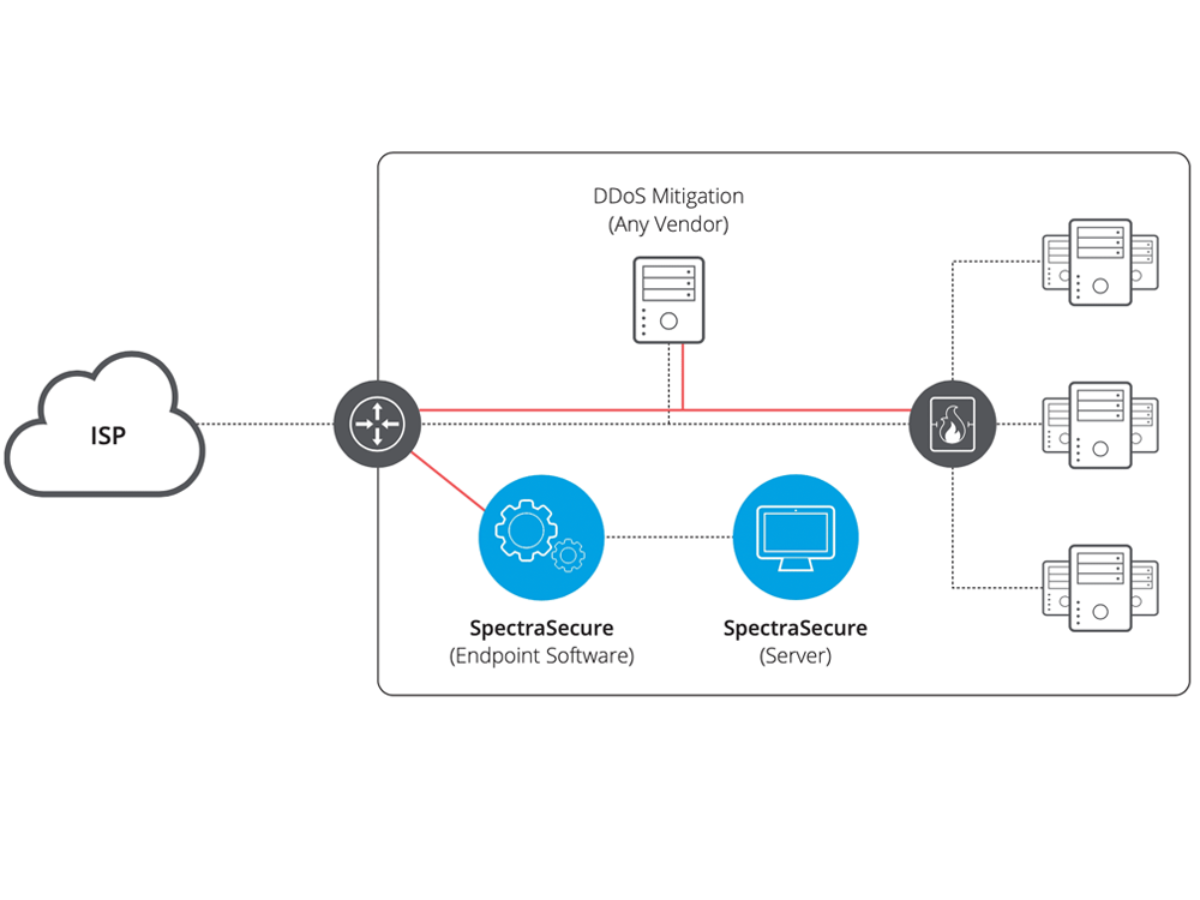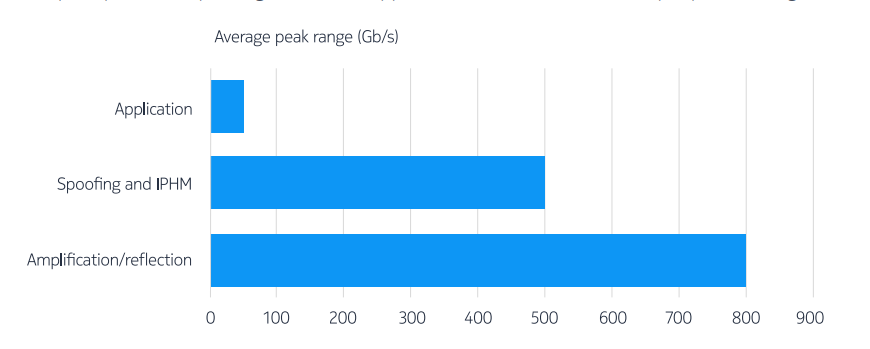
Symmetry | Free Full-Text | Distributed Denial of Service (DDoS) Mitigation Using Blockchain—A Comprehensive Insight
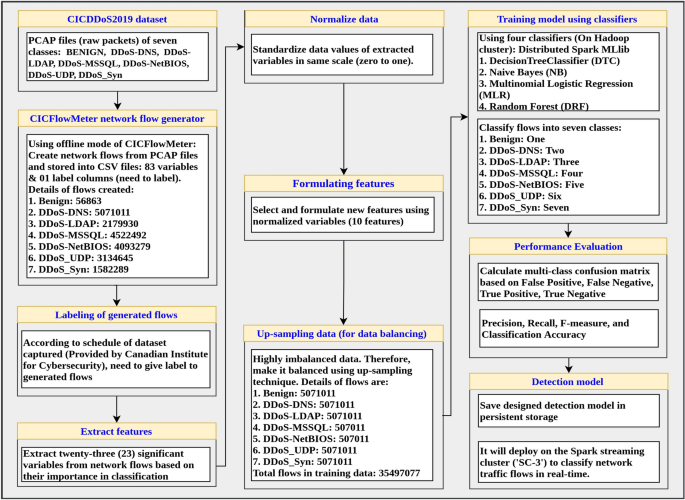
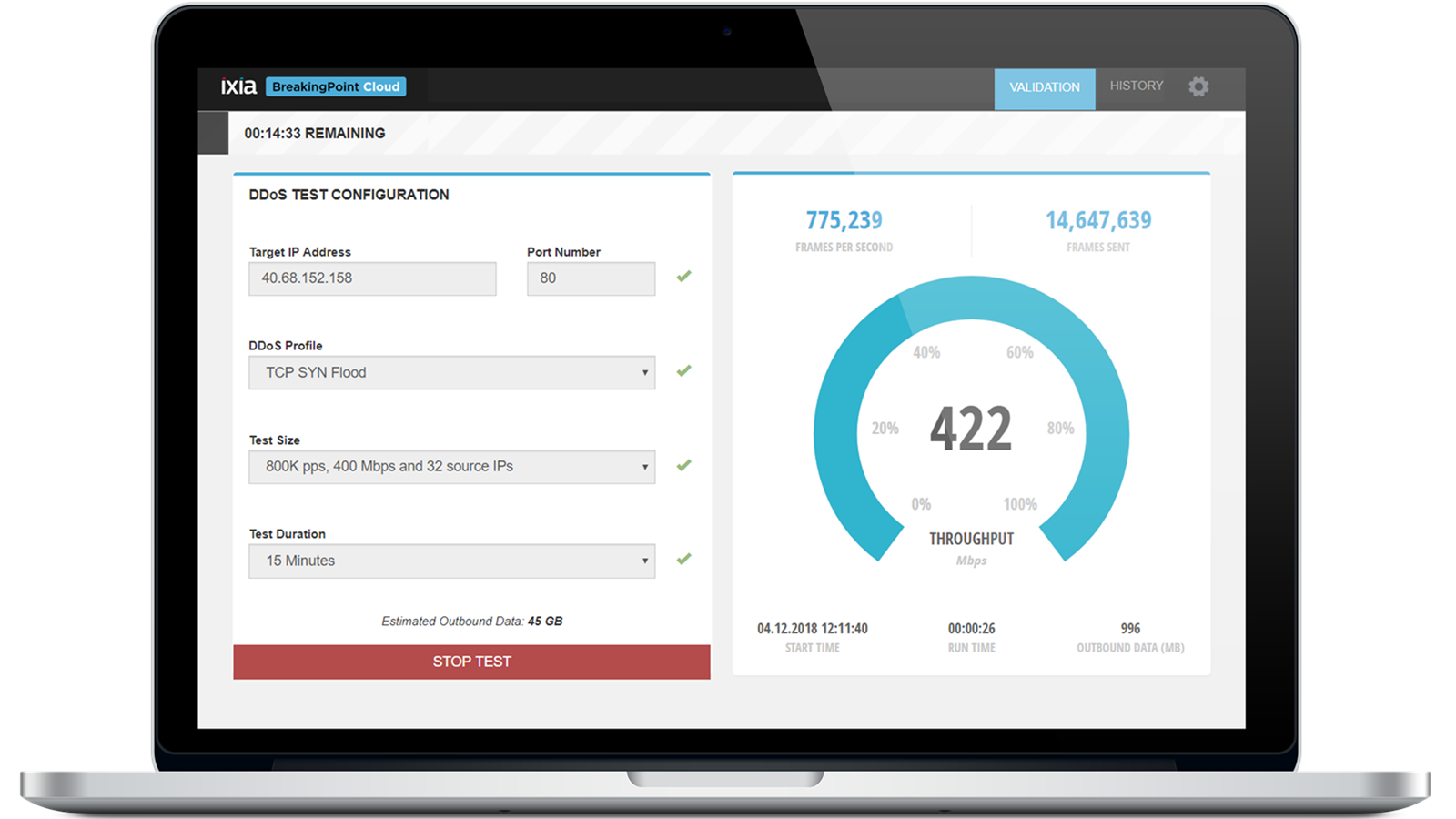
SSK-DDoS: distributed stream processing framework based classification system for DDoS attacks | SpringerLink
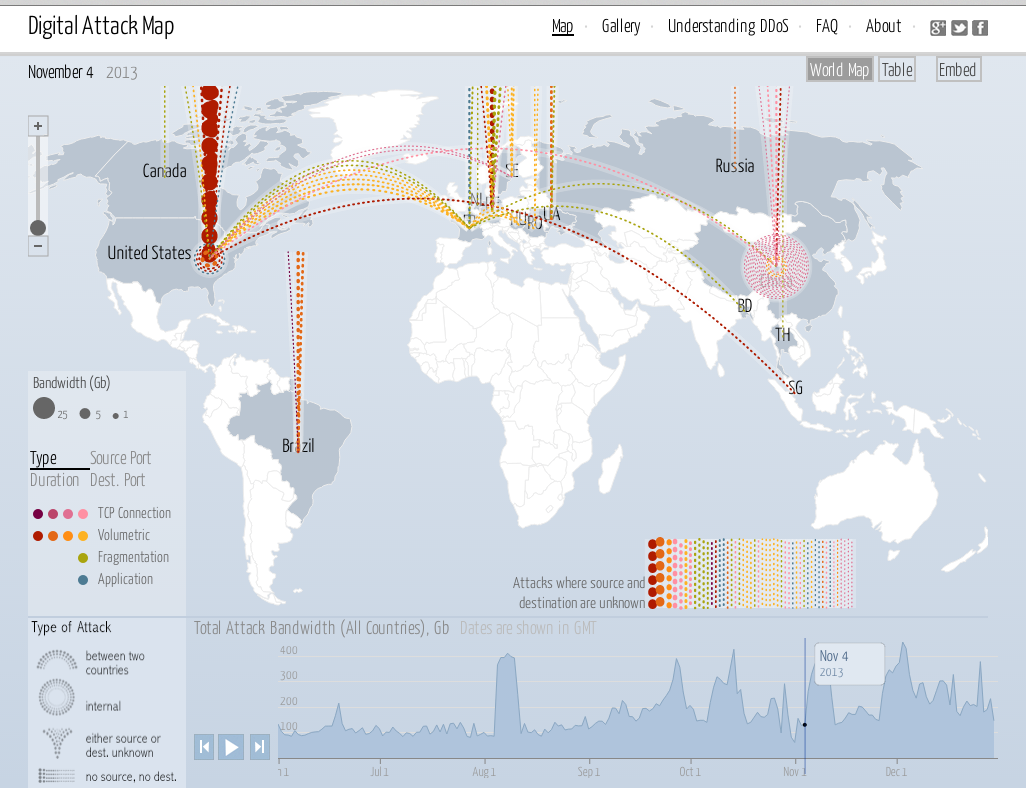
18 Hours of Disruption: How DDoS Attacks Plagued PokerStars' High Profile WCOOP Series | Poker Industry PRO
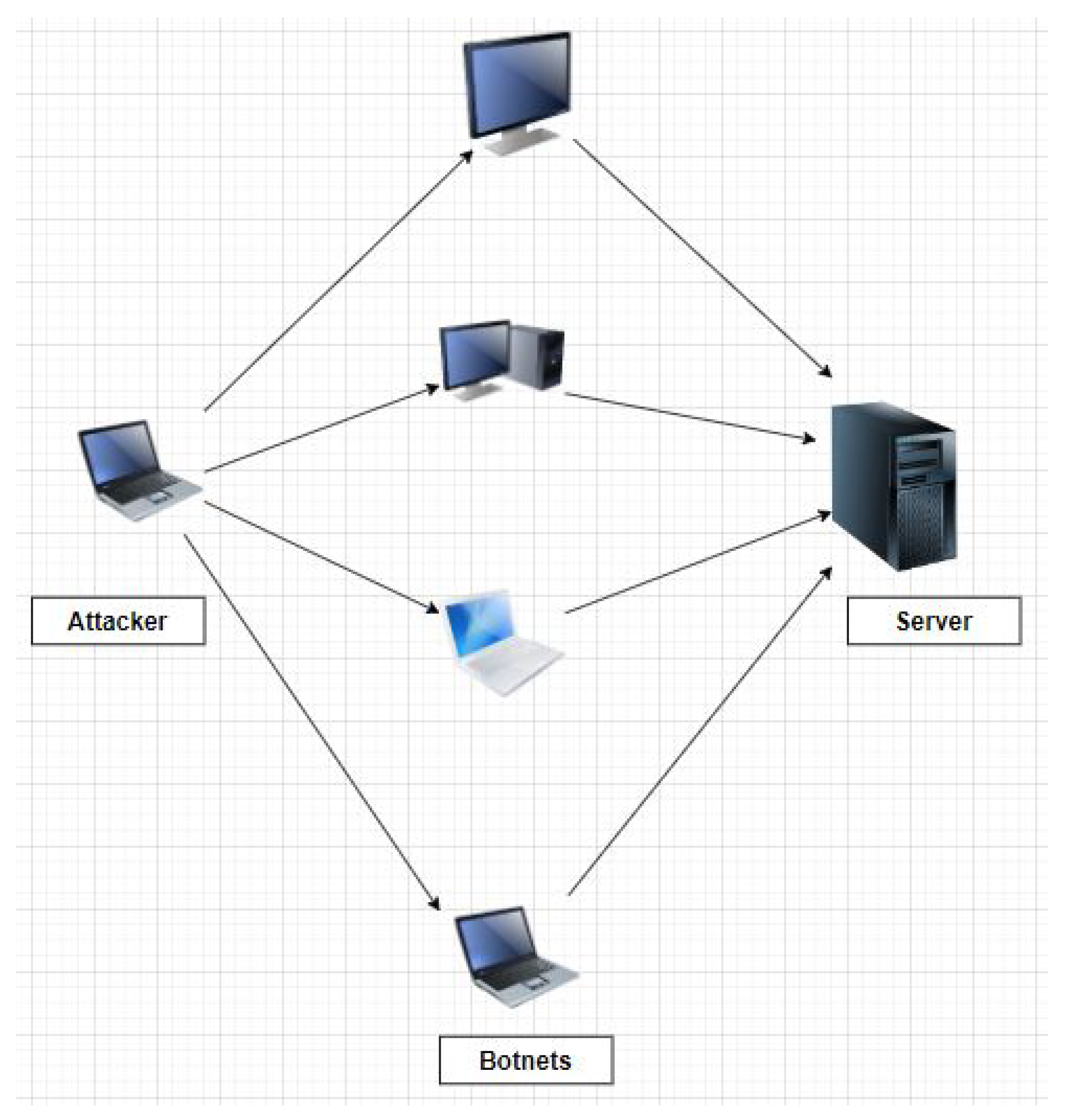
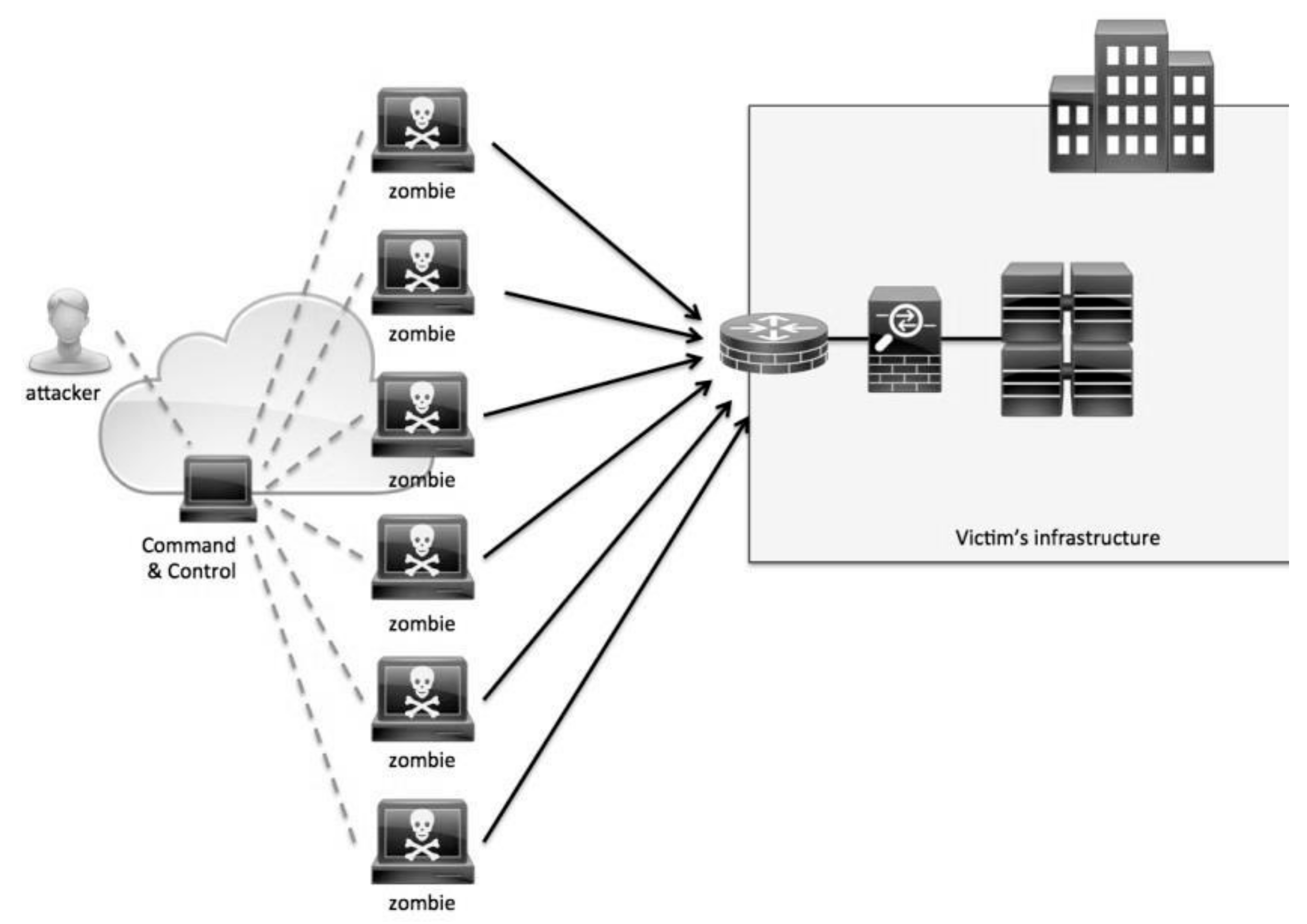
A DDoS attack scenario in IoT networks as a Botnet to target legitimate... | Download Scientific Diagram